Technology is integral to a child’s life. They will see it everywhere from birth and…
Change The Code And Start Again ~ This Is Not Over
World reels from massive cyber-attack that hit nearly 100 countries. What an excellent series of unfortunate events. But at the same time – ‘Accidental hero’ halts ransomware attack and warns: this is not over. Expert who stopped spread of attack by activating software’s ‘kill switch’ says criminals will ‘change the code and start again’. What is this all about? What happened?
What is Ransomware?
Ransomware is a type of malicious software that carries out the cryptoviral extortion attack from cryptovirology that blocks access to data until a ransom is paid and displays a message requesting payment to unlock it.
Simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse. More advanced malware encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them. The ransomware may also encrypt the computer’s Master File Table (MFT) or the entire hard drive. Thus, ransomware is a denial-of-access attack that prevents computer users from accessing files since it is intractable to decrypt the files without the decryption key. Ransomware attacks are typically carried out using a Trojan that has a payload disguised as a legitimate file.
Originating from Russia? Again? Smart ..
While initially popular in Russia, the use of ransomware scams has grown internationally; in June 2013, security software vendor McAfee released data showing that it had collected over 250,000 unique samples of ransomware in the first quarter of 2013, more than double the number it had obtained in the first quarter of 2012.
 Wide-ranging attacks involving encryption-based ransomware began to increase through Trojans such as CryptoLocker, which had procured an estimated US$3 million before it was taken down by authorities, and CryptoWall, which was estimated by the US Federal Bureau of Investigation (FBI) to have accrued over $18m by June 2015.
Wide-ranging attacks involving encryption-based ransomware began to increase through Trojans such as CryptoLocker, which had procured an estimated US$3 million before it was taken down by authorities, and CryptoWall, which was estimated by the US Federal Bureau of Investigation (FBI) to have accrued over $18m by June 2015.
But why then? The concept of file encrypting ransomware was invented and implemented by Young and Yung at Columbia University and was presented at the 1996 IEEE Security & Privacy conference. It is called cryptoviral extortion and is the following 3-round protocol carried out between the attacker and the victim.
The Accidental Hero
The ransomware used in Friday’s attack wreaked havoc on organisations including FedEx and Telefónica, as well as the UK’s National Health Service (NHS), where operations were cancelled, X-rays, test results and patient records became unavailable and phones did not work.
The “accidental hero” who halted the global spread of an unprecedented ransomware attack by registering a garbled domain name hidden in the malware has warned the attack could be rebooted.
But the spread of the attack was brought to a sudden halt when one UK cybersecurity researcher tweeting as @malwaretechblog, with the help of Darien Huss from security firm Proofpoint, found and inadvertently activated a “kill switch” in the malicious software.
As from The Guardian’s Article:
The researcher, who identified himself only as MalwareTech, is a 22-year-old from south-west England who works for Kryptos logic, an LA-based threat intelligence company.
“I was out having lunch with a friend and got back about 3pm and saw an influx of news articles about the NHS and various UK organisations being hit,” he told the Guardian. “I had a bit of a look into that and then I found a sample of the malware behind it, and saw that it was connecting out to a specific domain, which was not registered. So I picked it up not knowing what it did at the time.”
The kill switch was hardcoded into the malware in case the creator wanted to stop it spreading. This involved a very long nonsensical domain name that the malware makes a request to – just as if it was looking up any website – and if the request comes back and shows that the domain is live, the kill switch takes effect and the malware stops spreading. The domain cost $10.69 and was immediately registering thousands of connections every second.
MalwareTech explained that he bought the domain because his company tracks botnets, and by registering these domains they can get an insight into how the botnet is spreading. “The intent was to just monitor the spread and see if we could do anything about it later on. But we actually stopped the spread just by registering the domain,” he said. But the following hours were an “emotional rollercoaster”.
More Business for IT Security Industry?
Good news or not so good news: Cybersecurity spending is expected to reach $1 trillion over the next five years, according to the most recent Cybersecurity Ventures Market Report. This has raised the demand for security vendors, opening the door for new startup companies and growth for well-known firms.
However, just as there is no one-size-fits-all when it comes to security needs, cybersecurity vendors have different types of expertise, ranging from email security to anti-virus software to cloud security. Choosing the right vendor involves recognizing where your greatest cybersecurity requirements are and finding the best fit.
Beyond selecting a company, get a better understanding of how to prevent cybercrime by reading our guide to cyberthreat prevention. We explain how to reduce your risk of information loss, deal with employees leaving to join a competitor, and manage your data on the Internet or in the cloud.
Accidentally Stop a Global Cyber Attacks?
You’ve probably read about the WannaCrypt fiasco on several news sites but let’s see another side to the story. As MalwareTech was/is digging into the story, we can follow a very unusual and highly personal approach on the topic. Story includes many connotations, advertisements and city-IT-slang rhetorics and it follows like this:
On the malwaretech.com’s website, person writes:
I woke up at around 10 AM and checked onto the UK cyber threat sharing platform where i had been following the spread of the Emotet banking malware, something which seemed incredibly significant until today. There were a few of your usual posts about various organisations being hit with ransomware, but nothing significant…yet. I ended up going out to lunch with a friend, meanwhile the WannaCrypt ransomware campaign had entered full swing.
When I returned home at about 2:30, the threat sharing platform was flooded with posts about various NHS systems all across the country being hit, which was what tipped me of to the fact this was something big. Although ransomware on a public sector system isn’t even newsworthy, systems being hit simultaneously across the country is (contrary to popular belief, most NHS employees don’t open phishing emails which suggested that something to be this widespread it would have to be propagated using another method). I was quickly able to get a sample of the malware with the help of Kafeine, a good friend and fellow researcher. Upon running the sample in my analysis environment I instantly noticed it queried an unregistered domain, which i promptly registered.
The story reminds us a lot about “Can’t see the Genome article ..”
But author continues: Using Cisco Umbrella, we can actually see query volume to the domain prior to my registration of it which shows the campaign started at around 8 AM UTC.
While the domain was propagating, I ran the sample again in my virtual environment to be met with WannaCrypt ransom page; but more interestingly was that after encrypting the fake files I left there as a test, it started connecting out to random IP addresses on port 445 (used by SMB). The mass connection attempts immediately made me think exploit scanner, and the fact it was scanning on the SMB port caused me to look back to the recent ShadowBroker leak of NSA exploits containing….an SMB exploit. Obvious I had no evidence yet that it was definitely scanning SMB hosts or using the leaked NSA exploit, so I tweeted out my finding and went to tend to the now propagated domain. etc .. (picture below)
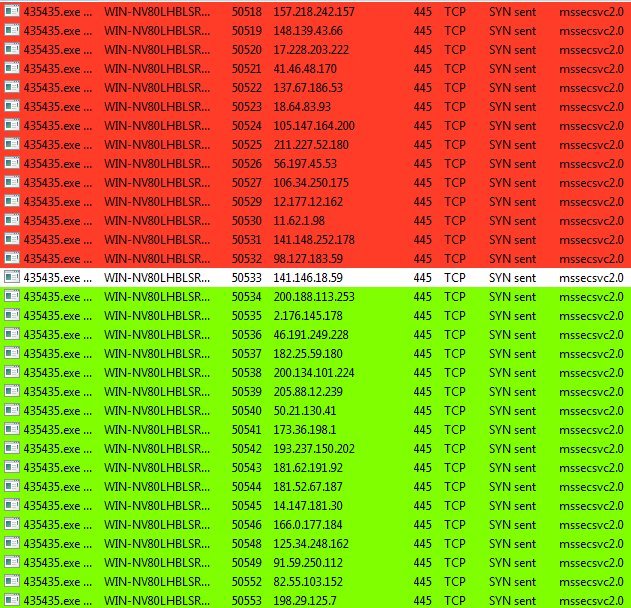
.. we will not continue with reproducing author’s story, but if you wish, follow the example here >
Microsoft, My Hero?
Microsoft has become Wall Street’s darling again after a few rough years in the late Steve Ballmer era. But the company still has a lot riding on executing well in 2017. First and foremost, Microsoft, under Satya Nadella—who stepped in as chief executive, replacing Ballmer about three years ago—must prove it can do big acquisitions well.
Now everyone is talking about the big release – and as the above author states: By releasing an out of bounds patch for unsupported operating systems such as Windows XP and Server 2003, people now are able to patch rather than having to attempt upgrades to newer system in order to be secured against this worm.
Microsoft’s record there is checkered following misfires with Nokia and aQuantive—both purchases resulting in huge write-offs. That means all eyes will be on how the software giant does with its just completed $26 billion purchase of LinkedIn.
There’s no shortage of opinions about where LinkedIn is weak. With a clunky interface, it incessantly nudges users to share information and interact with people they may or may not want to engage. Does anyone actually appreciate reminders to send holiday greetings to long-forgotten associates?
If any of the above, than you are my hero. Never a corporate interference and capital gain. And you, in this case, are the customer. With us you can trust. That sort of a game. See here >>
- Sale
Connect 365/7/24 Hourly Support
Original price was: $120.00.$99.00Current price is: $99.00. - Sale
Connect Auto-Pilot for WordPress Content Management
Original price was: $599.00.$499.00Current price is: $499.00. - Sale
%22%20transform%3D%22translate(1.8%201.8)%20scale(3.63281)%22%20fill-opacity%3D%22.5%22%3E%3Cpath%20fill%3D%22%23c2ffee%22%20d%3D%22M204.4%20130.6l1.2%2072-158%202.8-1.2-72z%22%2F%3E%3Cellipse%20fill%3D%22%23c4ffef%22%20cx%3D%22122%22%20cy%3D%2272%22%20rx%3D%2283%22%20ry%3D%2235%22%2F%3E%3Cellipse%20fill%3D%22%23beffea%22%20cx%3D%2265%22%20cy%3D%22126%22%20rx%3D%2235%22%20ry%3D%2256%22%2F%3E%3Cellipse%20fill%3D%22%2388ccb5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(51.92988%20-137.38378%2059.61857%2022.5353%20255%20209.3)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E) Select options This product has multiple variants. The options may be chosen on the product page
Select options This product has multiple variants. The options may be chosen on the product pageConnect WordPress Maintenance Plans
$99.00 – $224.00
6.
Change The Code And Start Again ~ This Is Not Over






