Armed with a mission to deliver a more secure internet, Yubico has been working closely with Microsoft, Google, the FIDO Alliance and W3C to create and drive open standards that pave the way for the future of passwordless login. The FIDO2 standard is the new standard enabling the replacement of weak password-based authentication with strong hardware-based authentication using public key (asymmetric) cryptography.
FIDO2 has created quite a buzz in the security community, and as with any new technology, there’s always a bit of a learning curve. Earlier this year, we introduced our updated Yubico Developer Program to help developers get up to speed quickly with FIDO2 and WebAuthn.
In the past few weeks, we have run a FIDO2 webinar series for developers to provide background on the FIDO2 specification and how to implement. During the course of this webinar series, we have answered many questions about the specifics of the FIDO2 standard and WebAuthn, including how it relates to our new Security Key by Yubico, and the evolution of a passwordless world. We wanted to share the most commonly asked questions and answers, that you also may have wondered about.
Are FIDO2 and WebAuthn the same thing? If not, how are they different?
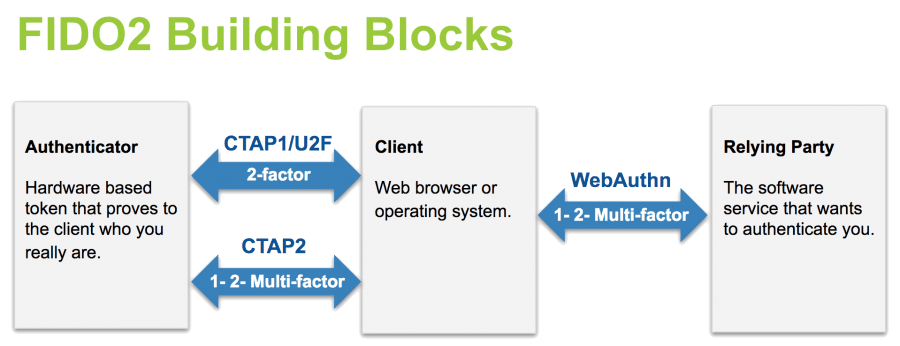
FIDO2 is comprised of two standardized components, a web API (WebAuthn) and a Client to Authenticator Protocol (CTAP). The two work together and are required to achieve a passwordless experience for login. The earlier FIDO U2F protocol working with external authenticators is now renamed to CTAP1 in the WebAuthn specifications.
With Chrome and Firefox announcing WebAuthn API and CTAP1 support as the client, and Dropbox now integrating with the WebAuthn API, this has kicked off a flurry of integration activities by other services. Most recently, Microsoft Edge released support for WebAuthn API, CTAP1 and CTAP2, making it the browser with the widest authentication support.
Is FIDO2 backwards-compatible with current YubiKey models?
The WebAuthn component of FIDO2 is backwards-compatible with FIDO U2F authenticators via the CTAP1 protocol in the WebAuthn specifications. This means that all previously certified FIDO U2F Security Keys and YubiKeys will continue to work as a second-factor authentication login experience with web browsers and online services supporting WebAuthn.
The new FIDO2 passwordless experience will require the additional functionally of CTAP2, which is currently only offered in the new Security Key by Yubico. CTAP2 is not supported in previous FIDO U2F Security Keys, or current YubiKey 4 series, or the YubiKey NEO.
Is FIDO2 considered single factor, two-factor or multi-factor authentication?
Login with a FIDO2-enabled hardware device, such as the Security Key by Yubico, offers a greater choice for strong authentication including:
- single factor passwordless
- two-factor (2FA)
- multi-factor authentication (MFA)
With FIDO2, a hardware-based authenticator — such as the Security Key by Yubico — can replace a username and password as a much stronger form of single factor authentication. Users can also continue to use the Security Key by Yubico as a second factor. Finally, for added security, a FIDO2 hardware authenticator can be combined with an additional factor, such as a PIN or biometric gesture, to enable strong multi-factor authentication.
How secure is FIDO2 compared to FIDO U2F and other 2FA solutions?
Single factor login with FIDO2 offers strong authentication as a single factor. In many cases, this single factor authentication is more secure than other forms of two-factor authentication (such as SMS), as there are no secrets that can be phished remotely when using FIDO2. FIDO2 single factor uses the same strong public key cryptography with origin checking to prevent phishing just like FIDO U2F, but with the additional convenience of not needing usernames and passwords as the first factor to identify the user.
Will FIDO U2F become obsolete with the expansion of FIDO2?
FIDO2 WebAuthn is backwards compatible with FIDO U2F authenticators, so over time, we expect FIDO2 will subsume FIDO U2F.
Is there an option to use FIDO2 in conjunction with an additional factor such as a pin or biometrics? Is this recommended?
Hardware authenticators supporting CTAP2 can add user verification by requiring users to use a PIN or biometric to unlock the hardware authenticator so it can perform its role. This preference is primarily dependent on the implementor’s threat vectors as well as use cases. For example, a large banking institution may want to consider the use of a PIN in conjunction with a security key for a higher level of assurance, while a warehouse-based shared kiosk environment may not.
The Security Key by Yubico is enabled with the full CTAP2 specs, and is fully enabled to support several passwordless experiences including single factor touch-and-go using the hardware authenticator (no need for a username) as well as use of a PIN with touch of the hardware authenticator.
What’s the difference between a PIN and password?
As stated above, one of the allowances with FIDO2 is the option to combine hardware-based authentication with an additional factor such as a PIN. This has many of you wondering, “Well, isn’t that the same as needing to remember a password?”
A PIN is actually different than a password. The purpose of the PIN is to unlock the Security Key so it can perform its role. A PIN is stored locally on the device, and is never sent across the network. In contrast, a password is sent across a network to the service for validation, and that can be phished. In addition, since the PIN is not part of the security context for remotely authenticating the user, the PIN does not need the same security requirements as passwords that are sent across the network for verification. This means that a PIN can be much simpler, shorter and does not need to change often, which reduces concerns and IT support loads for reset and recovery. Therefore, the hardware authenticator with a PIN provides a passwordless, phishing-resistant solution for authentication.
How does FIDO2 affect a company’s password policy of replacing passwords every 90 days?
With FIDO2, there’s no need to replace passwords, as there are no passwords required.
For those combining a hardware authenticator with a PIN, it’s important to note that PINs do not demand the same security requirement as a password. A PIN and a password are different. Since a PIN is not part of the security context for remotely authenticating the user (the PIN is not sent over the network for verification), it can be much simpler and less complex than a password, and does not need to be changed with the same frequency (or at all), which eases enterprise concerns about PIN reset and recovery.
What services provide support for FIDO2? When can we expect additional services to roll out support?
Chrome, Firefox, and Dropbox have implemented support for WebAuthn second-factor login flow. Beginning with build 17723, Microsoft Edge now supports the candidate release version of WebAuthn. This latest version of Edge is able to support FIDO2 strong single factor and multi-factor authentication, in addition to the second factor. The Yubico Developer Program offers comprehensive resources for those interested in adding support for FIDO2.
What if I lose my Security Key by Yubico? Without a password, am I locked out of my account?
Best practice is always to ensure that you have a backup Security Key in place, should you misplace your primary device. The Security Key by Yubico contains no identifiable information, so if it were to be found, it could not immediately be used to login without knowing the identity of the owner and to which accounts it is registered. The reality is that the primary attack vector for consumers and enterprises is remote account takeover — whether by credential theft, phishing scams, or man-in-the-middle attacks. FIDO2 and the Security Key by Yubico are specifically designed to protect against these types of threats.
For those who are concerned with physical threats, the option is there to require multi-factor authentication using a PIN for additional protection. That way, if someone obtains a stolen Security Key, they will still need to know which accounts it is registered with, and also have access to your additional factor (PIN) to be able to log in.
A significant benefit of an open authentication standard is that the number of implementations are limitless. With Microsoft Edge, Google Chrome and Mozilla Firefox working as the client and Dropbox working as the service, all have announced WebAuthn support with many more in the works. We’re well on our way to the future of passwordless login!
Do you want to be a part of the future of passwordless login?
If you are a developer who is interested in adding support for FIDO2, sign up for our Developer Program mailing list to stay up-to-date on workshops, webinars, implementation guides, reference code, APIs and SDKs. Also, our series of FIDO2 virtual events is now available for on-demand viewing.
If you’d like to read more about FIDO2, check out our recent blog post, “What is FIDO2?”